Why Digital Marketers Should Care About Log4j
By Vault JS | December 14, 2021

Digital marketing assurance requires you to keep an eye on all your marketing technologies. That’s already hard enough without also needing to understand what sorts of backend issues vendors might have, and how they might impact you. Should you be worried by the Log4j vulnerability? If so, what can you do about it?
What is Log4j?
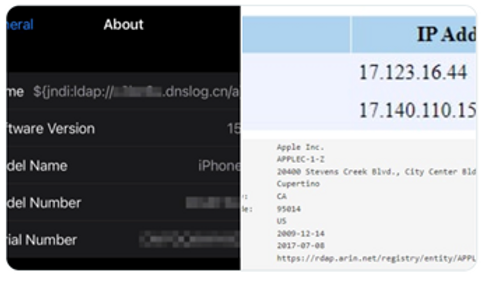
At a high level, Log4j is a common piece of code supported by one of the most trusted open source organizations in the world: Apache. The code is used to help handle logging in environments that send a lot of log data home for analysis. There aren’t many vulnerabilities worse than what happened with Log4j. It just takes a little bit of technical savviness for a hacker to get into any server running Log4j and then run their own code. That may sound scary—and it is.
For a real-world demonstration, check out this tweet from iPhone user @chvancooten demonstrating apple servers being (at the time) controllable. Disturbingly, while this issue only came to light December 10, 2021, the vulnerability existed since July 12, 2014!
Why You Should Care
Log4j is a common piece of code that exposes servers using it to the worst kind of vulnerability. Why should you care as a digital marketer? Because that same code could be in place when you put a third-party vendor’s code on your site, exposing your system to that same vulnerability. As an example, let’s consider a common vendor: Adobe Audience Manager. If you’ve deployed the AAM tag to your site, or any of your Adobe products deploy AAM hosted tags to your site, you need to find out if Adobe’s servers can be controlled by a hacker. If they are exposed, then the hacker can change the code that’s running on your site, and as a result they could deface your site or even steal data from your customers. Common attacks like Magecart require the attacker to get their code to run on your site, and this Log4j vulnerability gives the hackers a lot of opportunity.
Fortunately, in this particular example, Adobe says this problem has been “patched.” But there is no way to actually confirm your vendors have updated their code with the latest patch, whether it’s from Adobe or any other vendor.
What You Can Do
You could, and probably should, ask each of your affected vendors if they have updated their code, to help ensure your site’s safety, and protect your users. How can you find out which of the many marketing technologies on your site are impacted? The hard answer here is that it takes multiple overlapping areas of expertise to answer this question thoroughly. For example, if you’re using Adobe Audience Manager, you’d have to be an expert in the history and technology of the Adobe stack to understand that AAM code is sometimes hosted on the demdex.com domain. But just knowing that AAM code can come from demdex.com might not even be enough information. Sometimes, vendors will piggyback and package up their services. So, you might think you’re just deploying Adobe Campaign, but it could be piggybacking Audience Manager, which might have its own vulnerabilities. On top of all these confusing and jumbled potential relationships, you also need to be able to figure out if the underlying software your vendors use might also be vulnerable, which means being an expert on all the various technologies vendors use. That’s a lot of overlapping—and you need a nearly impossible-to-have level of expertise to figure it out.
Even when your vendors declare that they have addressed a known vulnerability, there is no way to independently verify it. The only thing you can do as a digital marketer is to monitor and analyze the actual code running on your site in case a vendor has been compromised from a vulnerability of log4j, or any other vulnerability. Obviously, that can be a daunting task.
Fortunately, Vault JS makes it easy.
At Vault JS, we not only provide the key data to answer many of these questions (such as, “what code is on my site?” and, “which code comes from which vendor?”), we also provide the overlapping security and marketing expertise to interpret the data for you. We find suspicious code changes to our customers’ sites, analyze them and proactively notify our customers when there are issues. Sure, tracking problems such as Log4j vulnerabilities would be nearly impossible for you and your team. But for Vault JS, it’s what we do.
Recent Posts
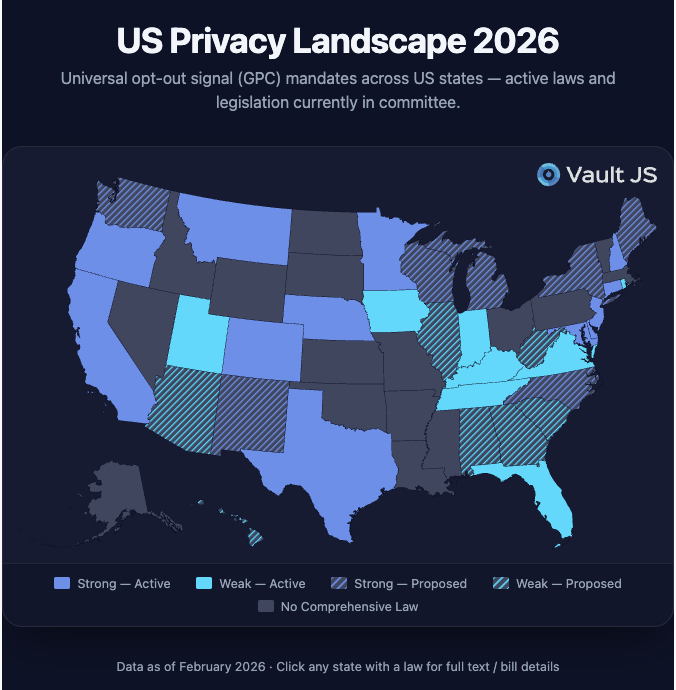
U.S. Privacy Laws (and Key Provisions) That Take Effect or Become Enforceable in 2026
Read More

CIPA: Why Old Statutes May Be the Strongest Force of Web Privacy
Read More
Shah v Capital One CCPA PRA Risk
At a recent privacy event for Chief Privacy Officers in Los Angeles California, it wasn’t the relatively non existent CCPA (California Consumer Privacy Act) enforcement...
Read More